Egress firewall rules control outgoing connections from target instances in your VPC network. Egress rules with an allow action permit traffic from instances based on the other components of the rule. For example, you can permit outbound traffic to specific destinations, such as a range of IPv4 addresses, on protocols and destination ports that you specify. Similarly, egress rules with a denyaction block traffic based on the other components of the rule.
■Stateful inspection Stateful inspection operates at the network and the transport layers of the OSI model, but it has the ability to monitor state information regarding a connection. Once the connection is deemed to be acceptable, the firewall remembers this. Therefore, subsequent traffic can be examined as either permissible or not within the context of the entire session. It then functions by checking each packet to verify that it is an expected response to a current communications session. Egress firewall rules example VM 1 has no specified egress firewall rule, so the implied allow egress rule lets it send traffic to any destination. Connections to other instances in the VPC network are allowed, subject to applicable ingress rules for those other instances.
VM 1 is able to send traffic to VM 4 becauseVM 4 has an ingress rule allowing incoming traffic from any IP address range. Because VM 1 has an external IP address, it is able to send traffic to external hosts on the internet. Incoming responses to traffic sent by VM 1 are allowed because firewall rules are stateful.
Ingress rules with an allow action permit incoming traffic based on the othercomponents of the rule. In addition to specifying the source and target for the rule, you can limit the rule to apply to specific protocols and destination ports. Similarly, ingress rules with a deny action can be used to protect instances by blocking incoming traffic based on the firewall rule components. SNMP assists spiteful users to learn too much about a system, making password speculations easier. SNMP is often disregarded when checking for vulnerabilities due to the User Datagram Protocol ports 161 and 162. Ensure network management servers are physically secured and secured on the network layer.
Consider utilizing a segregate management subnet, protecting it by using a router with an access list. Unless the service is required, it should be shut off by default. This eliminates the possibility of any obscure protocols being utilized, while minimizing the danger of an incident.
Key among that information is the "interesting ports table". That table lists the port number and protocol, service name, and state. The state is either open, filtered, closed, or unfiltered. Open means that an application on the target machine is listening for connections/packets on that port. Filtered means that a firewall, filter, or other network obstacle is blocking the port so that Nmap cannot tell whether it is open or closed.
Closed ports have no application listening on them, though they could open up at any time. Ports are classified as unfiltered when they are responsive to Nmap's probes, but Nmap cannot determine whether they are open or closed. Nmap reports the state combinations open|filtered and closed|filtered when it cannot determine which of the two states describe a port.
The port table may also include software version details when version detection has been requested. When an IP protocol scan is requested (-sO), Nmap provides information on supported IP protocols rather than listening ports. The forwarding rule alone determines which protocols and ports are accepted by the proxy load balancer. When you create a VPC firewall rule, you specify a VPC network and a set of components that define what the rule does.
The components enable you to target certain types of traffic, based on the traffic's protocol, destination ports, sources, and destinations. Binary archives can only be used on a target system running MacPorts. They allow MacPorts utilities to skip the build and begin installation after the destroot phase.
Binary archives are automatically created whenever a port is installed, and can also be downloaded from a server. MacPorts runs a buildbot infrastructure that creates prebuilt binary packages for all ports in MacPorts for the default installation prefix. Buildbots exist for systems later or equal to Snow Leopard.
If you have access to a computer outside your network, you can download and install a security application that will enable you to scan all ports on the router and computers connected to it. To use the applications on an outside computer, though, you will need to provide access to the internal network to the IP address of the system with the scanning application. You can open access to the network in the configuration settings of the router. Monitor current traffic for which IP addresses and ports are used — and validate that they are needed; not everything requires internet access. If you are replacing a firewall, you can create a span port or look at the old firewall logs to determine this.
Compile a list of the source IP, destination IP, and destination port and start to group them into categories for easier firewall rule creation. When configuring firewall rules it is highly recommended to allow remote connections on the inter-node communication port from every cluster member and every host where CLI tools might be used. Epmd port must be open for CLI tools and clustering to function. It is designed to operate rapidly by either allowing or denying packets simply based on source and destination IP address and port information.
This is the simplest and fastest form of traffic-filtering firewall technologies. Some malicious software acts as a service, waiting for connections from a remote attacker in order to give them information or control over the machine. This knowledge provides you a starting point for figuring out what Internet traffic to permit through the firewall, and what to deny. Occasionally a MacPorts developer may wish to install more than one MacPorts instance on the same host.
Only one copy of MacPorts may use the default prefix /opt/local, so for additional installations use the option --prefix as shown below. It's also recommended to change the applications dir using --with-applications-dir to avoid conflicts in /Applications/MacPorts. Use --without-startupitems to automatically set startupitem_install noin the new macports.conf, which is required to avoid conflicts in /Library/LaunchAgents or /Library/LaunchDaemons. In TCP/IP and UDP networking, ports are endpoints for logical communications. A single IP address may have many services running, such as a web server, an application server, and a file server. In order for each of these services to communicate, they each listen and communicate on a specific port.
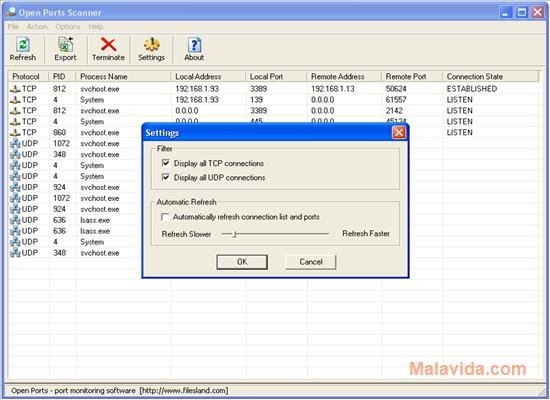
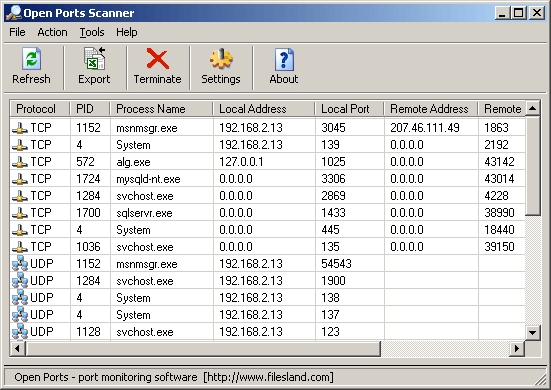
When you make a connection to a server, you connect to the the IP address and a port. An application is actively accepting TCP connections, UDP datagrams or SCTP associations on this port. Finding these is often the primary goal of port scanning.
Security-minded people know that each open port is an avenue for attack. Attackers and pen-testers want to exploit the open ports, while administrators try to close or protect them with firewalls without thwarting legitimate users. Open ports are also interesting for non-security scans because they show services available for use on the network.
What ports should not be open You can narrow the scope of a firewall rule by specifying protocols or protocols and destination ports. You can specify a protocol or a combination of protocols and their destination ports. If you omit both protocols and ports, the firewall rule is applicable for all traffic on any protocol and any destination port. One thing to keep in mind is that when we discuss ports in terms of a firewall, we usually refer to traffic coming in on a specific port. For instance, when we talk about FTP traffic on port 21, we are not talking about someone using an FTP client to connect to another FTP site.
We are talking about a host running an FTP server where inbound connections are made to port 21, or in other words, the FTP server listens to port 21. Typically, a router protects your network from the outside world by limiting external access to your internal network. But some devices and programs like IP cameras and online games need a connection from the internet that's not blocked by a firewall. In most cases, port forwarding and port opening are configured automatically between your Wifi devices and your connected devices using UPnP.
It is essential to know that Mac OS X opens ports as per requests by individual applications or services instead of managing ports individually. Most users using the default OS X firewall should use the following steps to Allow incoming connections for Applications. They must also configure their routers to forward incoming packets to the appropriate server. The following diagram illustrates some examples where firewall rules can control egress connections. The examples use the targetparameter in rule assignments to apply rules to specific instances. The following diagram illustrates some examples where firewall rules can control ingress connections.
Google Cloud implements connection tracking regardless of whether the protocol supports connections. If a connection is allowed between a source and a target or between a target and a destination , all response traffic is allowed as long as the firewall's connection tracking state is active. A firewall rule's tracking state is considered active if at least one packet is sent every 10 minutes. VPC firewall rules let you allow or deny connections to or from your virtual machine instances based on a configuration that you specify. Enabled VPC firewall rules are always enforced, protecting your instances regardless of their configuration and operating system, even if they have not started up. The private, or dynamic, port numbers are used by clients and not servers.
Datagrams sent from a client to a server are typically only sent to well-known or registered ports . Server applications are usually long lived, while client processes come and go as users run them. The server has no trouble replying to the proper client because the server can just reverse the source and destination port numbers to send a reply to the correct client . In order for the LDM system to send data to a downstream LDM, the firewall rules must allow incoming TCP connections to the port on which the LDM server is listening .
Ports exist either in allow mode, or deny (closed; blocked) mode. If your mail server is in a state of readiness to receive SMTP traffic, we call that "listening on port 25." That means port 25 is open. The main reason you interject a firewall between the Internet and your system is to get in the way of outsiders trying to access open ports. The applications on your network's machines can open ports without waiting for your knowledge or permission.
Some, like peer-to-peer file sharing or video conferencing software, open ports with the single-minded obsession of a frenzied border collie. Each of those open ports becomes another potential hole in your security, gullibly accepting whatever is sent to it, unless you take proactive steps to block it. Configuration for passive FTP on an MX appliance requires some additional knowledge of the FTP application. An ephemeral port is a temporary, non-registered port used for communication.
Ephemeral ports are typically high numbered and outside the range of IANA registered ports. To use an external load balancer without the routing mesh, set --endpoint-modeto dnsrr instead of the default value of vip. Instead, Docker sets up DNS entries for the service such that a DNS query for the service name returns a list of IP addresses, and the client connects directly to one of these. You are responsible for providing the list of IP addresses and ports to your load balancer.
If a port needs to use Xcode (i.e., xcodebuild) in any way, use_xcode yes should be set or the port should include the xcode PortGroup. The environment variable DEVELOPER_DIR is now exported during all build phases, set to the value of $ which may be the directory of Xcode or CLT depending on use_xcode. This means that libxcselect shims (i.e., /usr/bin/clang) will resolve to Xcode/CLT.
Build systems that ignore the environment may accidentally use Xcode which will cause a failure in trace mode. Those installing MacPorts from source code must modify their environment manually using the rules as a guide. A number of ports are safe to open such as the ones used for Internet access, email and FTP file transfers.
Common port numbers that typically may be open include 21, 25, 80, 110, 139 and 8080. By default, these port numbers are usually active and open in most routers. Many more might need to remain open because of legitimate applications installed on computers connected to the network.
VM 2 has no specified ingress firewall rule, so the implied deny ingress rule blocks all incoming traffic. Connections from other instances in the network are blocked, regardless of egress rules for the other instances. Because VM 2 has an external IP, there is a path to it from external hosts on the internet, but the implied deny ingress rule blocks external incoming traffic as well. There are a maximum number of target service accounts, source service accounts, target network tags, and source network tags that can be specified for firewall rules.
The firewall rule applies only to instances that use a specific service account. For the maximum number of target service accounts that you can apply per firewall rule, seeVPC resource quotas. The highest priority rule applicable to a target for a given type of traffic takes precedence.
IPv6 connections are also supported in VPC networks that have IPv6 enabled. When specifying a source for an ingress rule or a destination for an egress rule by address, you can specify IPv4 or IPv6 addresses or blocks in CIDR notation. The rule for firewalls, especially inbound traffic, is block everything, and only permit traffic to specific devices and services that you allow. By default, nothing outside of the US can talk to me, and I can't talk to anything outside of the US.